Privileged Access Management
Out do the Attackers
with PAM
Privileged Access Management
“74% of security breaches involve compromised privileged credentials. – Forbes"
Privileged Access Management (PAM) lets super-user access to users to control critical computer systems, applications, and servers anywhere at any time.
PAM solutions discrete privileged accounts such as system administration accounts, from an existing Active Directory and stores them in a secure repository to lessen the risk of credentials from theft. By creating a central repository of privileged credentials, PAM provides the highest level of cybersecurity, controls the user access, track all-access. It also monitors for any type suspicious activity.
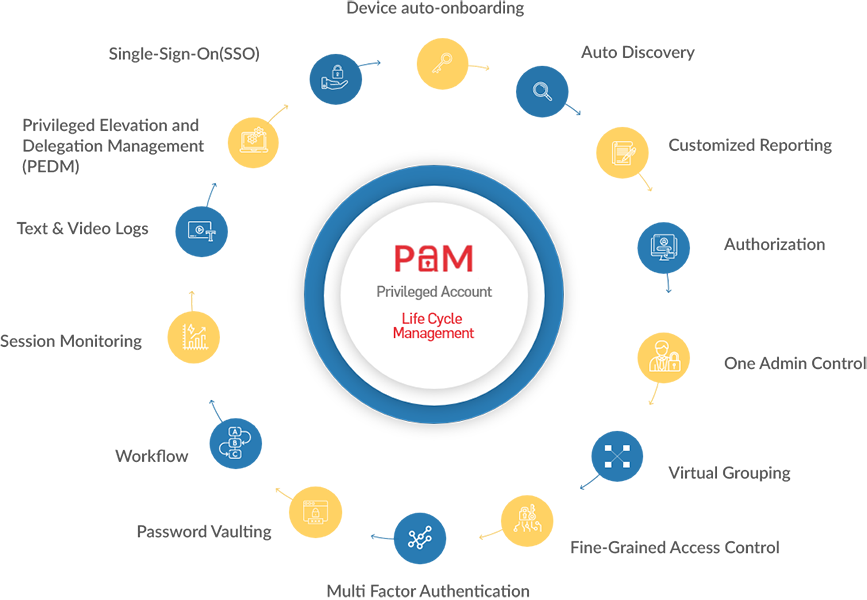
Features of Privileged Access Management
As attackers are seeking for vulnerable passwords to gain access into critical data, PAM has become important tool for companies having large, complex IT systems.
Our PAM tools and systems are delivered with the following features.

PASM - Privileged Account & Session Management
PEDM - Privilege Elevation & Delegation Management


Securing Privileged Remote Access
Auditing File & System Changes

Our PAM Offerings
Password Vault
S.M.A.R.T. Audit Trails
Session Recording
Granular Access Control
Virtual Grouping
AD Bridging
Solution Benefits
Taqadom’s Offerings
On-site and Offshore Model
Dedicated Support
On-Demand
Support
Testing
Solution/Process Consulting
Upgrade
On-Premise/Cloud Services
Implementation
Taqadom has partnered with Arcon, a leading information technology company specialized in risk control solutions, to provide top-of-the-range risk management services.
Arcon offers a proprietary unified governance framework, which addresses risks across various technology platforms. In the last decade, Arcon has been at the forefront of innovations in risk control solutions, with its roots strongly entranced in identifying business risk across industries. It is in a unique position to react with innovative solutions and products.


